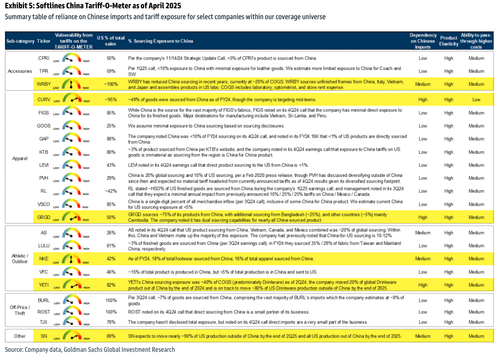
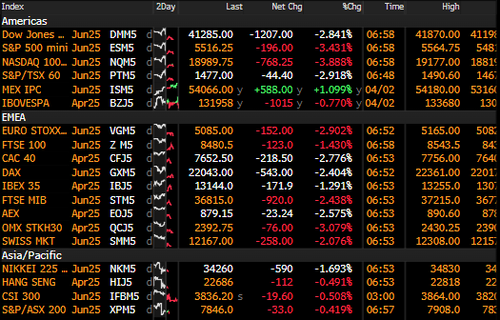
Can We Fix Our Demographic Doom Loop?
Can We Fix Our Demographic Doom Loop?
Authored by Edward Ring via American Greatness,
Throughout the developed world, birth rates have crashed.
But the “population bomb” that author Paul Ehrlich warned us about in the 1970s still exists; it’s just confined to the nations with the lowest per capita income. The correlation is almost perfect. The average number of children per woman in extremely poor nations is still extremely high.
For example, births per woman in Niger stand at a world-leading 6.6, which means that every generation the population of that nation will more than triple. Meanwhile, the per capita income in Niger, even based on purchasing power parity, stands at a dismal $2,084 per year. Exponential national population growth is occurring across most of the African continent, where in 1950, the population was estimated at around 225 million compared to an estimated 1.5 billion today. By 2050, Africa’s population is estimated to rise to 2.5 billion and is not estimated to level off until 2100 at nearly 4 billion people.
There are pockets of fecundity elsewhere in the world, primarily in the Middle East, but if you exclude Africa and some Islamic nations, the entire global population is on a path to oblivion. From China (1.2 children per woman), Korea (0.9), and Japan (1.3) to Germany (1.5), Italy (1.3), and the United Kingdom (1.6), populations are on track to descend by 50 percent in at most two generations. The European numbers are only slightly better than the Asian numbers because of immigration.
Because of the sensitive nature of the information, it is difficult to get reliable statistics on the birth rates of indigenous European women. But according to official data from the German government, nearly 50 percent of all children under the age of five in Germany have a “migration background.” Since 80 percent of Germany’s population is still reported as having “German origin,” it is clear that immigrant birthrates are far higher than the birthrates of indigenous German women.
This pattern repeats itself throughout the European nations and nations of European origin. According to the Office of National Statistics in the United Kingdom, the most common name for baby boys is now Muhammad. In the hopefully more assimilative United States, according to Pew Research, “minority” births now outnumber white births.
What these demographic trends portend for our future is central to every major issue we face. Can we maintain economic health if we accept a population in terminal decline? So far, the Asians are betting they can, relying on automation and AI to fill the labor gaps. Can we maintain cultural stability if we import Africans and Moslems to have babies since we don’t want to anymore? That’s the bet the European nations are making.
But there is an even more fundamental question that ought to be the topic of massive public debate, without stigmatizing the participants or restricting the theories offered up. Why don’t women in developed nations want to have babies anymore?
Answers to this question typically travel into safe spaces.
It’s economics: the cost of living is too high. Or the slightly conspiratorial but increasingly mainstream explanation that endocrine disruptors in our food and water…